In today’s digital landscape, ensuring robust cybersecurity measures is paramount. Ethical hackers play a crucial role in this endeavor, employing penetration testing tools to identify and rectify vulnerabilities before malicious actors exploit them. In this comprehensive guide, we’ll delve into the top 10 penetration testing tools favored by ethical hackers, equipping you with the knowledge to fortify your digital defenses effectively.
Table of Contents
Understanding pen testing
Before we delve into the specifics of the top tools, let’s first understand the concept of penetration testing. Also known as pen testing, it involves simulating cyberattacks to evaluate the security of systems, networks, and applications. Ethical hackers employ various techniques and tools to identify potential vulnerabilities, allowing organizations to proactively address security flaws and mitigate risks.
What is Penetration Testing?
Penetration testing, often abbreviated as pen testing, is a proactive cybersecurity measure that involves simulating cyberattacks to identify and address vulnerabilities within systems, networks, and applications.
Importance of pen testing
Penetration testing plays a crucial role in bolstering cybersecurity defenses by uncovering potential vulnerabilities and weaknesses before they can be exploited by malicious actors. By conducting regular pen tests, organizations can proactively enhance their security posture and safeguard sensitive data from cyber threats.
Exploring the Top 10 pen testing Tools for Ethical Hackers
Now, let’s explore the top 10 penetration testing tools that ethical hackers rely on to assess and fortify cybersecurity defenses:
1. Metasploit
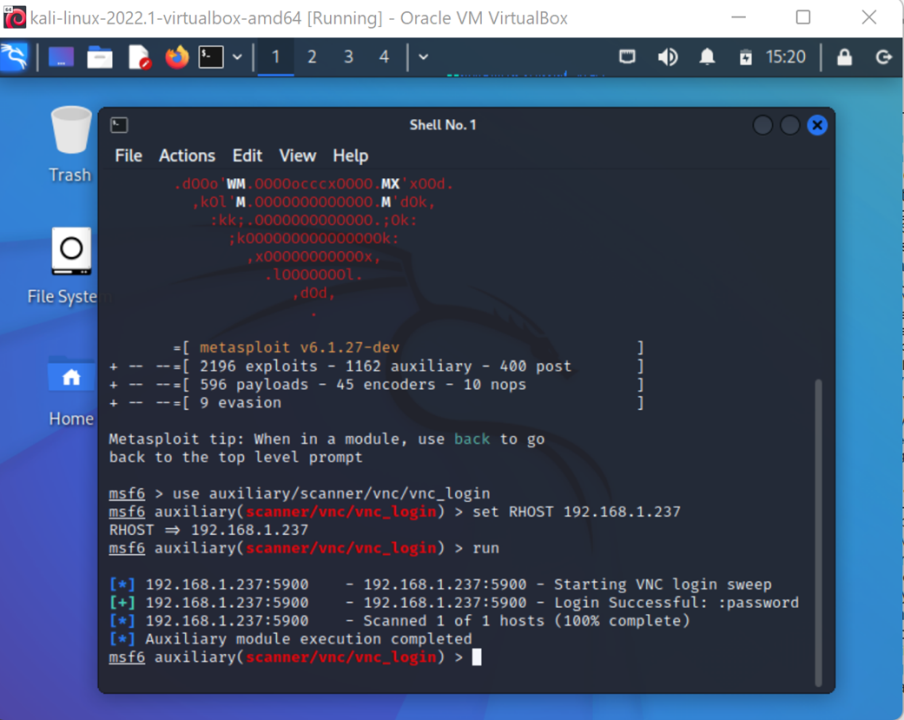
Metasploit is a powerful framework that offers a comprehensive suite of tools for penetration testing, exploit development, and vulnerability research. It provides a user-friendly interface and a vast array of exploits, making it a preferred choice among ethical hackers worldwide.
2. Nmap (Network Mapper)

Nmap, short for Network Mapper, is a versatile tool used for network discovery and security auditing. It enables users to identify hosts, services, and open ports on a network, providing valuable insights into potential security vulnerabilities.
3. Wireshark
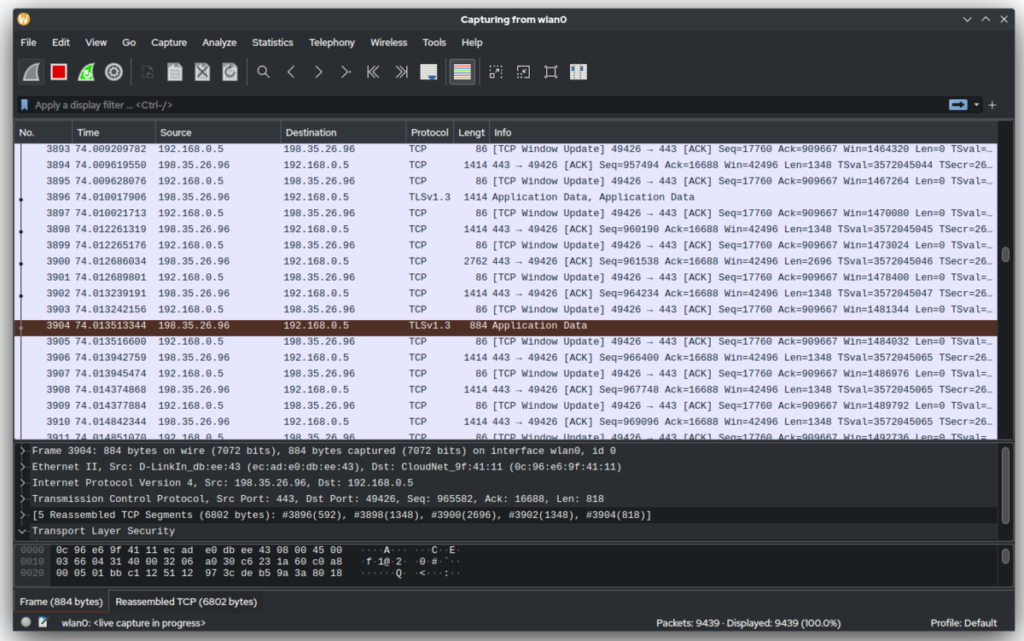
Wireshark is a renowned network protocol analyzer that allows users to capture and interactively browse the traffic running on a computer network. Ethical hackers leverage Wireshark to analyze network protocols, troubleshoot network issues, and detect suspicious activities.
4. Burp Suite

Burp Suite is a leading web application security testing tool used by ethical hackers to assess the security of web applications. It offers advanced scanning capabilities, interception proxies, and numerous other features that facilitate comprehensive security testing.
5. Aircrack-ng

Aircrack-ng is a suite of wireless network security tools that enables ethical hackers to assess the security of Wi-Fi networks. It includes tools for packet capturing, password cracking, and network analysis, making it indispensable for wireless security assessments.
6. John the Ripper

John the Ripper is a widely used password cracking tool that employs various techniques, including dictionary attacks and brute force attacks, to uncover weak passwords. Ethical hackers utilize John the Ripper to assess the strength of passwords and enhance password security.
7. Nikto

Nikto is an open-source web server scanner that helps ethical hackers identify and remediate security vulnerabilities in web servers. It performs comprehensive scans for outdated software, misconfigurations, and other common issues, allowing organizations to fortify their web server security.
8. SQLMap

SQLMap is a powerful tool for detecting and exploiting SQL injection vulnerabilities in web applications. Ethical hackers use SQLMap to automate the process of identifying and exploiting SQL injection flaws, thereby enhancing the security of web applications.
9. Hydra

Hydra is a fast and flexible password-cracking tool that supports various protocols, including HTTP, FTP, and SSH. It allows ethical hackers to launch brute force and dictionary attacks against login credentials, helping organizations identify and mitigate weak passwords.
10. Nessus

Nessus is a comprehensive vulnerability scanning tool that enables ethical hackers to identify, assess, and remediate security vulnerabilities across networks, systems, and applications. It offers extensive vulnerability detection capabilities and intuitive reporting features, making it a valuable asset for cybersecurity professionals.
Also Read : Discover the Top 10 Trends for 2024
Frequently Asked Questions (FAQs)
Q: What are penetration testing tools? A: Penetration testing tools are software applications and frameworks used by ethical hackers to identify and address security vulnerabilities within systems, networks, and applications.
Q: Why is penetration testing important? A: Penetration testing is crucial for identifying potential security weaknesses before they can be exploited by malicious actors, thereby enhancing the overall cybersecurity posture of organizations.
Q: How do ethical hackers use penetration testing tools? A: Ethical hackers leverage penetration testing tools to simulate cyberattacks and identify vulnerabilities within systems, networks, and applications. By conducting thorough assessments, they help organizations proactively mitigate security risks.
Q: Are penetration testing tools legal? A: Yes, penetration testing tools are legal when used by authorized professionals for legitimate security testing purposes. However, it’s essential to obtain proper authorization before conducting any penetration testing activities.
Q: Can penetration testing tools cause damage to systems? A: While penetration testing tools are designed to identify vulnerabilities without causing harm, there is always a risk of unintended consequences. It’s crucial for ethical hackers to exercise caution and follow best practices to minimize the risk of system damage.
Q: How often should penetration testing be performed? A: Penetration testing should be conducted regularly, ideally on an annual or biannual basis, to ensure that cybersecurity defenses remain robust and effective against evolving threats.







